Event Log: log information viewable in Xeoma interface
As we’ve mentioned before, security systems rely on logging when it comes to analyzing data, checking for potential loopholes and post-breach damage control. However, all those benefits are only relevant long-term, which begs the question: are there any immediate benefits to them as well? Xeoma’s answer to that question is the new feature available as of version 21.8.3 – Event Log. This article will focus on how it works and how to apply it practically.
How it works
The log info can be found in Main menu → Information → Event log, here is what it looks like:
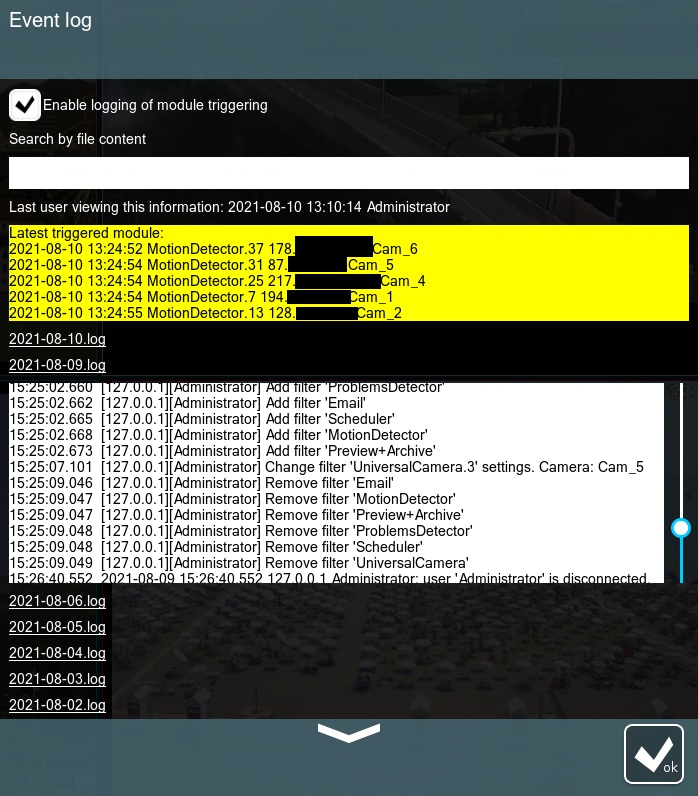
Here is a rundown of its content:
- Enable logging of module triggering – by default the log only keeps track of the changes in settings (adding, modifying, removing modules) and connections/disconnections; by checking this box we’ll force the log to record various detectors triggering on cameras.*
- Search by file content – if you already know the name of a given event but don’t know when it happened, you can indicate it here and Xeoma will find the relevant log/logs.
- Last user viewing this information – indicates the name of the last user that has been accessing the next point on this list along with the exact time; by default only Administrator is allowed to access the Event Log, however, other users may be granted such permission by the Administrator via Main menu → Remote access → Users (Enable viewing the program log through the interface checkbox).
- Latest triggered module> – it lists 5 last times any of the detectors were triggered by indicating the date and time for the trigger, the exact module’s ID and the name of the corresponding camera.
- .log files – these show the current content of the log-files without the need to open them separately.
*A word of caution: if various detectors on your server get triggered often, the logs will grow in size substantially with this option enabled. By default, Xeoma does not delete any logs, no matter how old they might be, so it would be prudent to clean particularly old files out from the Logs directory periodically either by hand, or with a script.
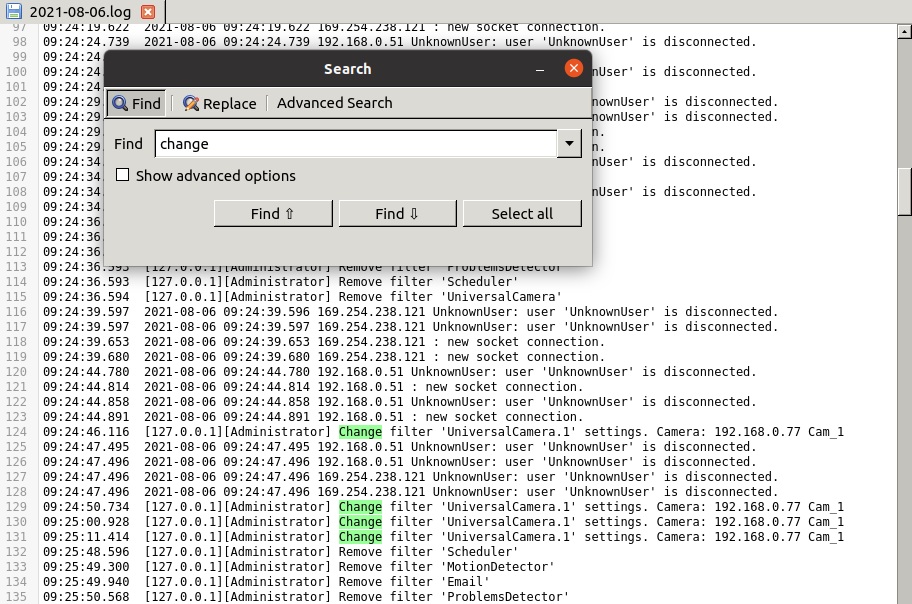
The final point on this list deserves a closer look, since there is a lot of log info present in this window making it important to know how to read them properly. Here are some of the most common lines in the logs:
14:10:34.820 [192.168.1.13][JeremyS] is logged.
A user named JeremyS connected to the server from a client device with the address 192.168.1.13 at exactly 14:10:34.820 (based on the server’s time zone).
14:35:33.326 2021-08-06 14:35:33.326 192.168.1.13 JeremyS: user 'JeremyS' is disconnected.
A user named JeremyS that was connected to the server from a client device with the address 192.168.1.13 disconnected from the server at exactly 14:35:33.326 on 2021-08-06.
11:55:18.624 [192.168.1.25][Administrator] Change filter 'Scheduler.12' settings. Camera: 192.168.10.11 Office_cam
The Administrator for this server, while connected from a client device with the address 192.168.1.25, changed the settings for the Scheduler module (exact module ID is Scheduler.12) from the chain of modules belonging to the camera with the following source name: 192.168.10.11 Office_cam. This was done at exactly 11:55:18.624.
N.B. Some module IDs may not have the exact same name as the module itself, see this table for reference.
13:38:20.296 Active module: 2021-08-06 13:38:20 AutoNumberPlateRecognition.44 194.56.10.18 Parking_cam
On 2021-08-06 at exactly 13:38:20.296 the ANPR module (exact module ID is AutoNumberPlateRecognition.44) was triggered on the camera with the following source name: 194.56.10.18 Parking_cam.
How to use
There are many ways to use the Event Log, here are some of the most common among them:
- Alarm monitor – keep a separate monitor in a security station where the Event Log is always displayed; this way the guards can always check the recent triggers of various detectors, so they’ll have a way of knowing that something happened, even if they missed it on the camera screen.
- Efficiency evaluation – the person in charge of security can check the log info to analyze the security response to a real or simulated breach; by checking who was viewing the Event Log, the time of the event and the time of the response they can measure how well the security team handled the breach.
Event Log is a versatile tool that allows you to keep the whole system under tight control, both short-term and long-term.
16 September, 2021
Read also:
Xeoma on VM and Docker
How to avoid failures with a video security system